PonyFinal – What Microsoft Users Need to Know About the Newest Ransomware

Microsoft’s security team announced that a new type of ransomware has been detected, and that Microsoft users should remain vigilant for possible vulnerabilities or hackings.
Ransomware is a type of malicious software that infects your devices through a variety of means, such as email attachments or links. The process often involves some form of social engineering, as criminals target specific individuals or businesses they believe to be weak points, and manipulate these people into paying money for their information to not be leaked – hence the name “ransom.”
We’re taking a look at what we currently know about this latest version of ransomware, and how you can keep your devices and data safe.
What is PonyFinal?
On May 27th, security experts on Microsoft’s Security Intelligence team shared on Twitter what they currently know about PonyFinal ransomware.
“PonyFinal is Java-based ransomware that is deployed in human-operated ransomware attacks. While Java-based ransomware is not unheard of, they’re not as common as other threat file types,” said Microsoft on their Twitter.
This particular strain of ransomware is referred to as human-operated, which means there are people manually setting off attacks and break-ins, as opposed to more familiar ransomware which is triggered by clicking on malicious links or attachments. Also, because it’s Java-based ransomware, PonyFinal attackers are more likely to target companies that already have Java Runtime Environment (JRE) installed. If not, they’ll install it themselves – but if a company already has it, they can move quicker without raising alarm.
So far, PonyFinal has been found in countries such as Iran, India and the United States, and it’s currently going after businesses instead of individuals. The cybercriminals using PonyFinal do their homework – they research specific businesses to attack and tailor their strategy and payload accordingly.
Microsoft’s security team has stated that so far, these attacks begin on a company’s systems management server. Once found, PonyFinal cyberhackers will use systematic attacks that help them guess weak passwords to gain entrance to the server. (This is why it’s important to use strong, unique passwords and keep them safe in a reliable password manager.)
"Ultimately, after they've gone through and understood the environment, they'll deploy ransomware of the attackers' choice that matches up most closely with the environment that they have observed over time,” says Phillip Misner, research director with Microsoft Threat Protection.
How Does PonyFinal Work?
Knowing that ransomware attacks can sometimes be hard to grasp, Microsoft created a visual to help business owners understand how PonyFinal works, and how quickly it can infiltrate their systems.
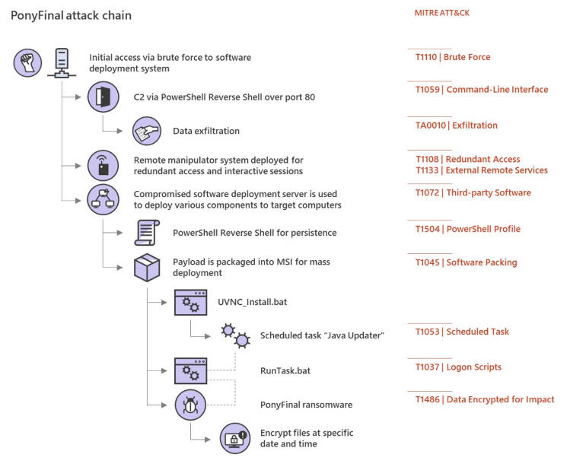
Once the PonyFinal cyberhackers are able to gain access to your company’s server, they’ll employ a specific code known as visual basic script and use it to set off a PowerShell, which consists of a collection of commands that trigger certain tasks. This allows the cyberhackers to steal localized data and install “a remote manipulator system to bypass event logging.”
Like other ransomware, PonyFinal is then used to encrypt your files, change their names and leave a ransom note. According to PCRisk, PonyFinal renames all of your files and adds on the ".enc" extension. So, if you had an image named 1.jpg, it would now be 1.jpg.enc.
In every folder with encrypted files, you’ll most likely find a ransom note entitled README_files.text, which reads as the following:
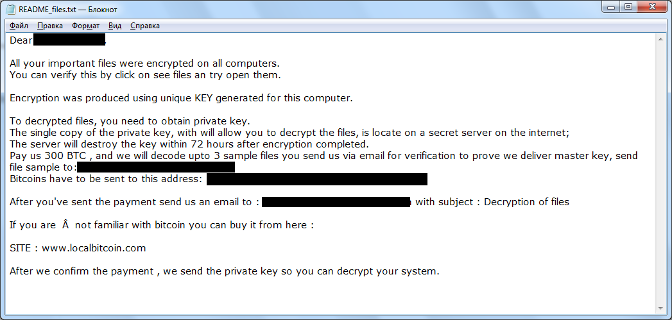
Source: ZDNet, Andrew Ivanov
If you’re at this point where your files are encrypted, your important information is inaccessible and you’re being asked to pay to get them back, it may be tempting to give in and pay the criminals. We strongly recommend you resist this urge.
Here’s What to Do If Your Company is Attacked
Our advice? Do not pay cybercriminals.
Along with there being no guarantee that cybercriminals might just refuse to unlock your data even after payments have been made (or decide they’d like even more money), there is the possibility that technological mistakes may have made it impossible to restore your system anyway. You could be paying for nothing.
To make matters worse, these criminals are increasingly targeting backups first. Modern, increasingly sophisticated ransomware not only locks up your system but also any networks your devices are connected to. This includes cloud storage and servers.
If you’ve received a PonyFinal ransom note, it’s important to take these steps:
· Disconnect your machine from other devices, larger company networks and external backups
· Take a screenshot, or use a camera or smartphone to take a picture of the ransom note to send to your IT provider, alerting them of the possible attack
In order to avoid being the victim of ransomware schemes, it’s important to enable secure passwords and two-factor authentication, a tiered approach to remote external backups and proper training so your staff can spot future signs of attack.










